Advent Of CyberSecurity 2
Task 22 : [Day 17] Reverse Engineering ReverseELFneering
Let us ssh into the target and see what we’ve got.
we have 2 binaries here, file1 is just for the tutorial , we will be looking at challenge1
Let us analyse it with radare2
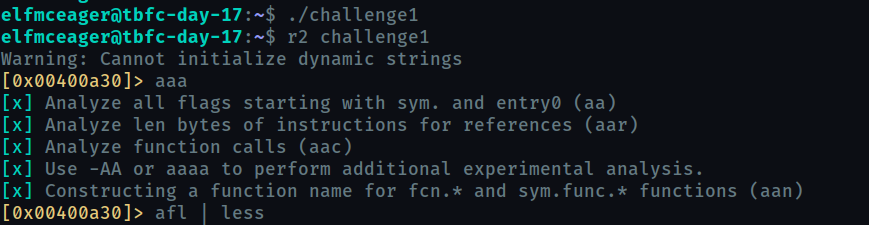
We used aaa to analyze the binary and we can see the list of functions using afl . We find that sym.main function is present. So we decompile it
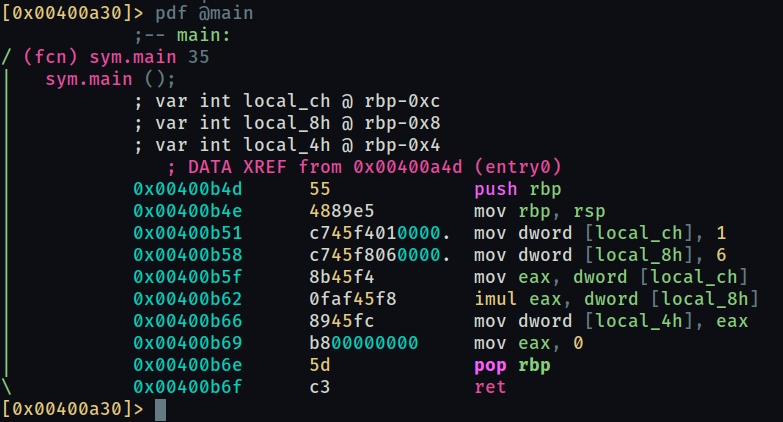
What is the value of local_ch when its corresponding movl instruction is called (first if multiple)?
1
mov dword [local_ch], 1 instruction moves 1 into the local_ch variable
What is the value of eax when the imull instruction is called?
6
mov dword [local_8h], 6 moves 6 into local_8h and imul eax, dword [local_8h] multiplies previous value of 1 and local_8h (1 x 6) and stores it into eax
What is the value of local_4h before eax is set to 0?
6
mov dword [local_4h], eax stores value of eax (6) into local_4h
Task 23 : [Day 18] Reverse Engineering The Bits of Christmas
I’ll use Remmina to connect to target using RDP
if you do not have it already , you can install it as ,
sudo apt install remmina
enter the target ip and then username password provided
Now open the TBFC app, try to enter any password… and unless you somehow guessed the right password you must get this dialog box
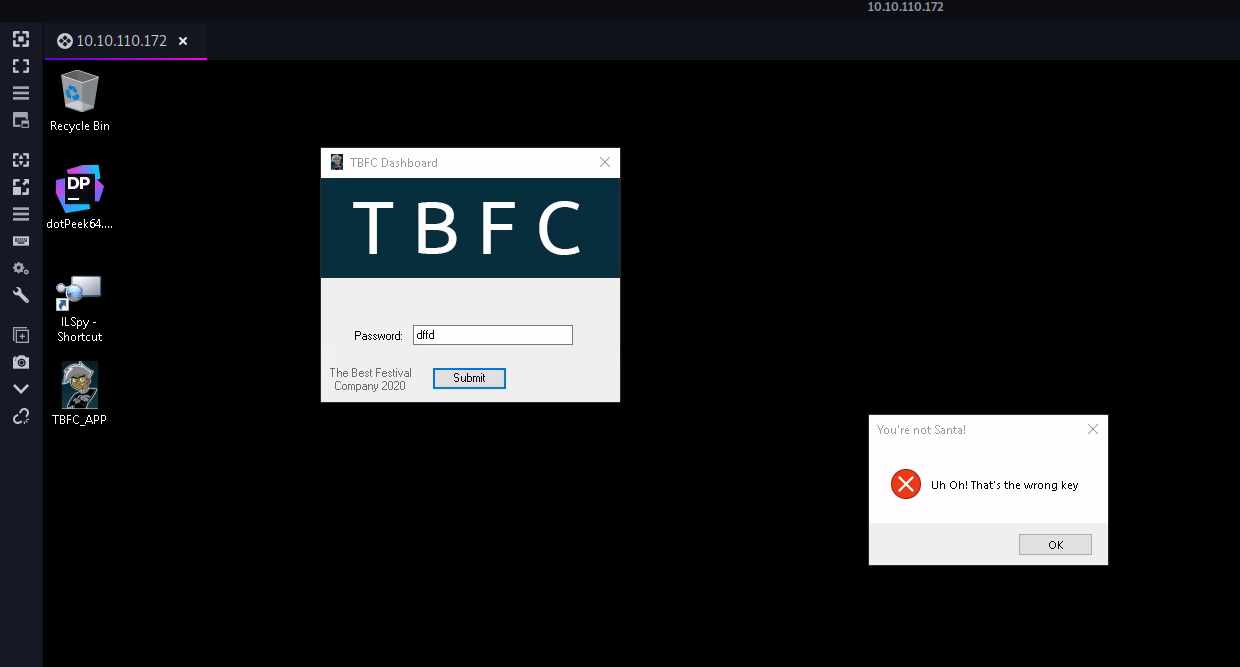
Now lets look at what is going behind the scenes in this application.
Fire up the IL Spy app and open the TBFC_APP in it
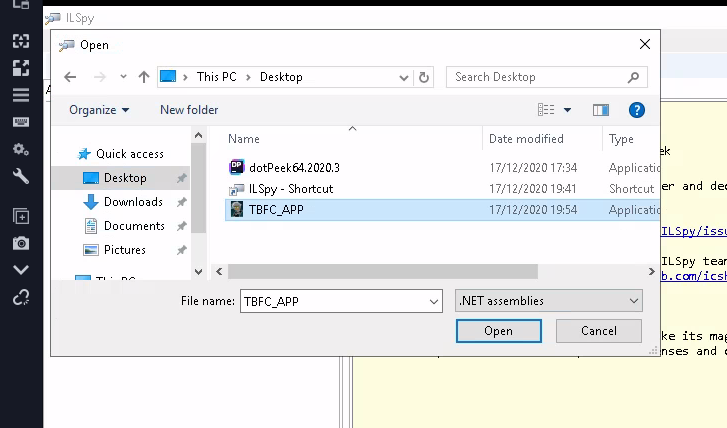
Crackme section sticks out of many items in the app
We can find the password logic if explore around a bit. I found the password check logic in the MainForm
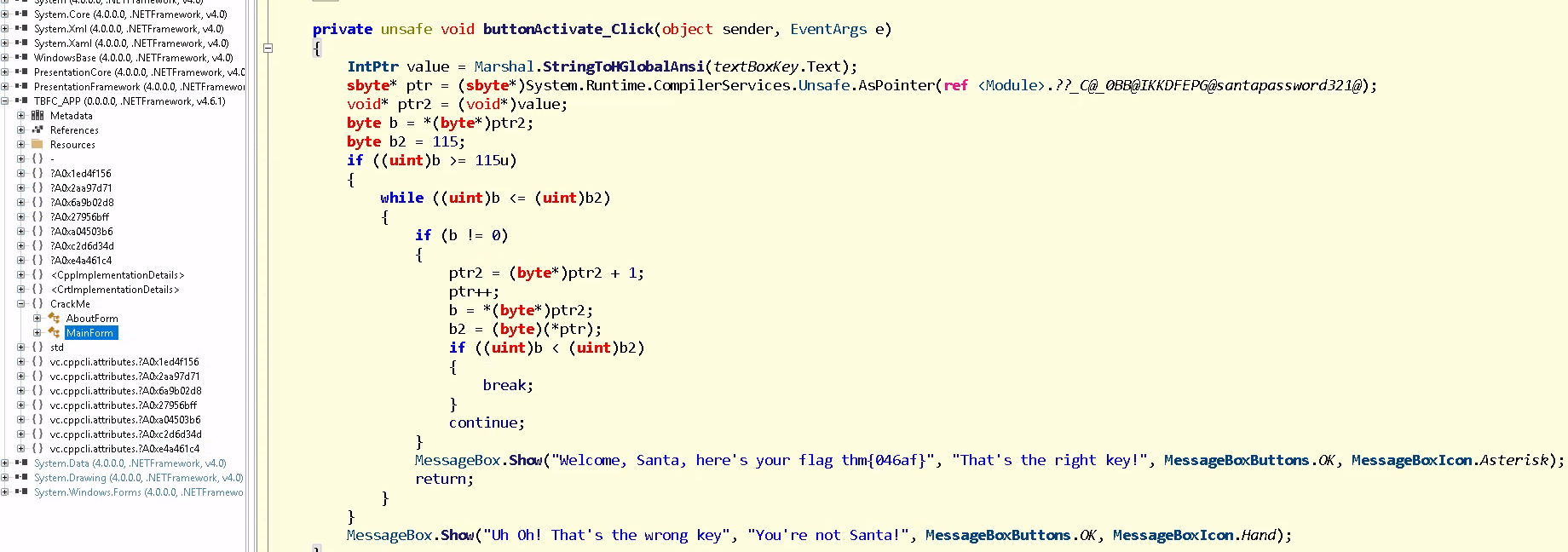
Here we find the value of the flag, also there seems to be a string named santapassword let us check that out by double clicking
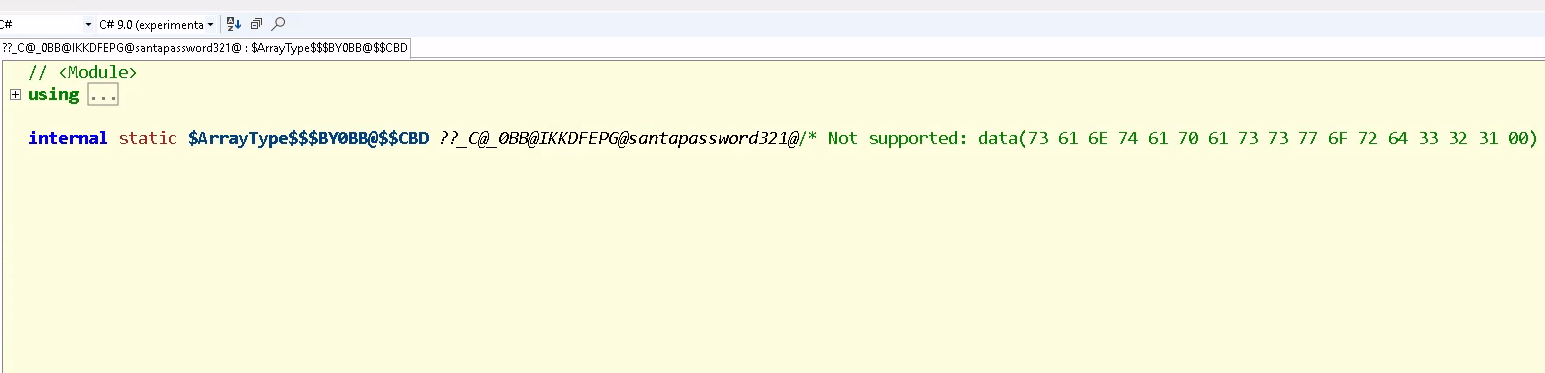
we get a hexadecimal constant which translates to santapassword321 which infact is our password
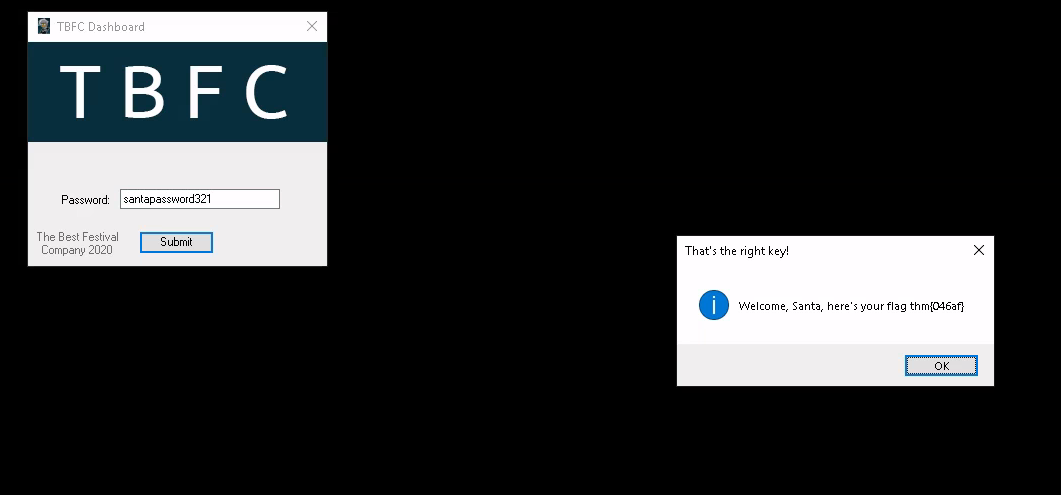
nice stuff